[CTI] Phish me if you can
Recently, I received quite an unusual phishing email.
At first, it looks like a typical delivery phishing, but it came from… a government address!

It came from the doctor appointment service from the Serbian Ministry of Health:
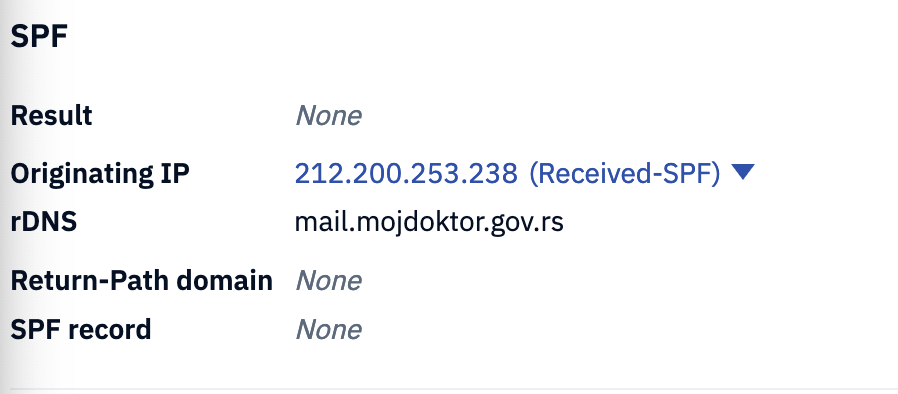
This domain has no DMARC policy in place, meaning it could be more easily beings used to spread malicious emails.
The email is simply an image rendered by HTML, and linked 2 fraudulent files:
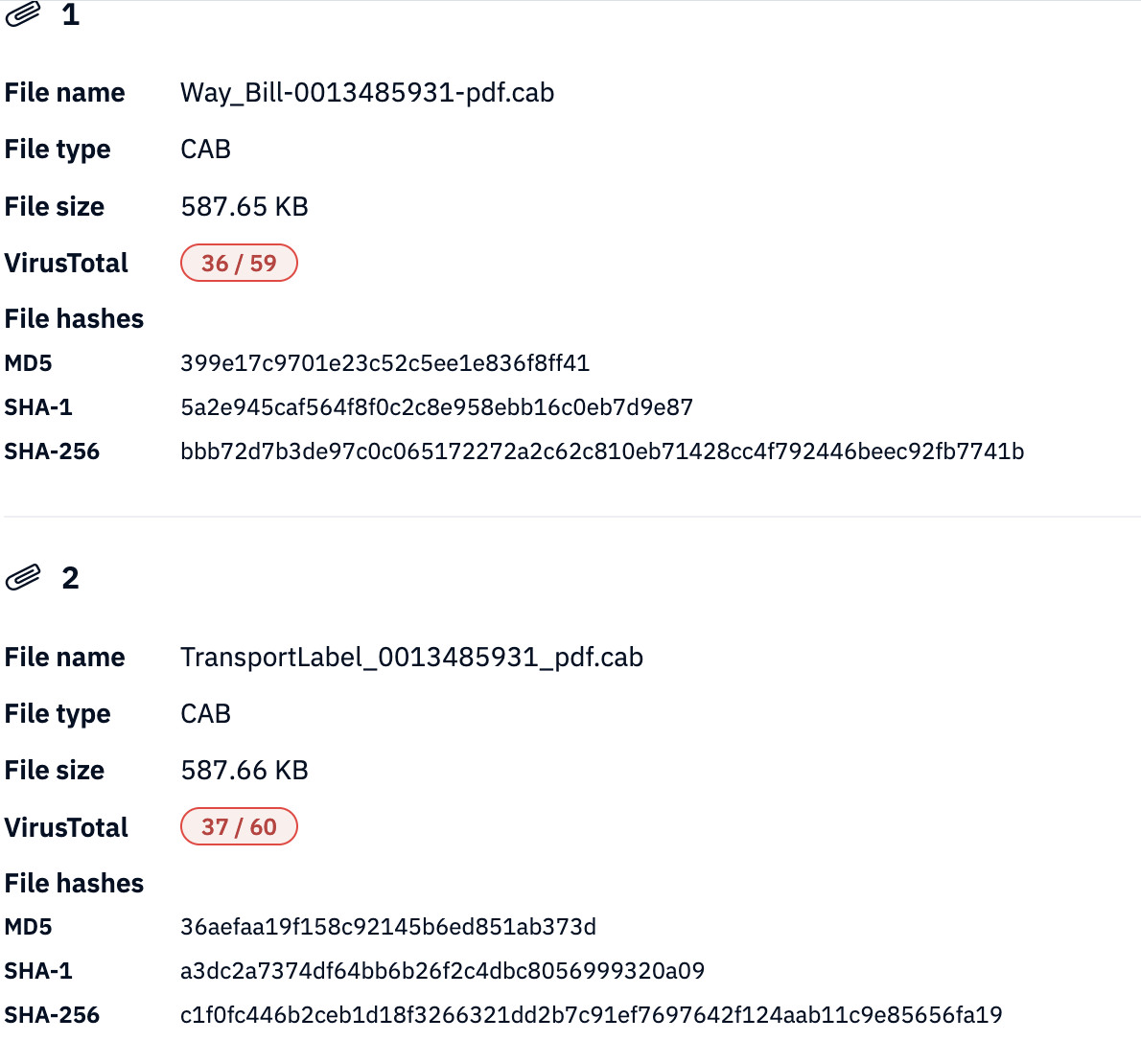
The files are named like:
- Way_Bill-0013485931-pdf.cab
- TransportLabel_0013485931_pdf.cab
A .cab file is simply a cabinet file, which is a type of archive file format used by Microsoft Windows for the storage and distribution of software programs and other data.
Here, the cab files are malicious and acting as trojan.
The domain mojdoktor.gov.rs has already been listed as sharing malicious files:
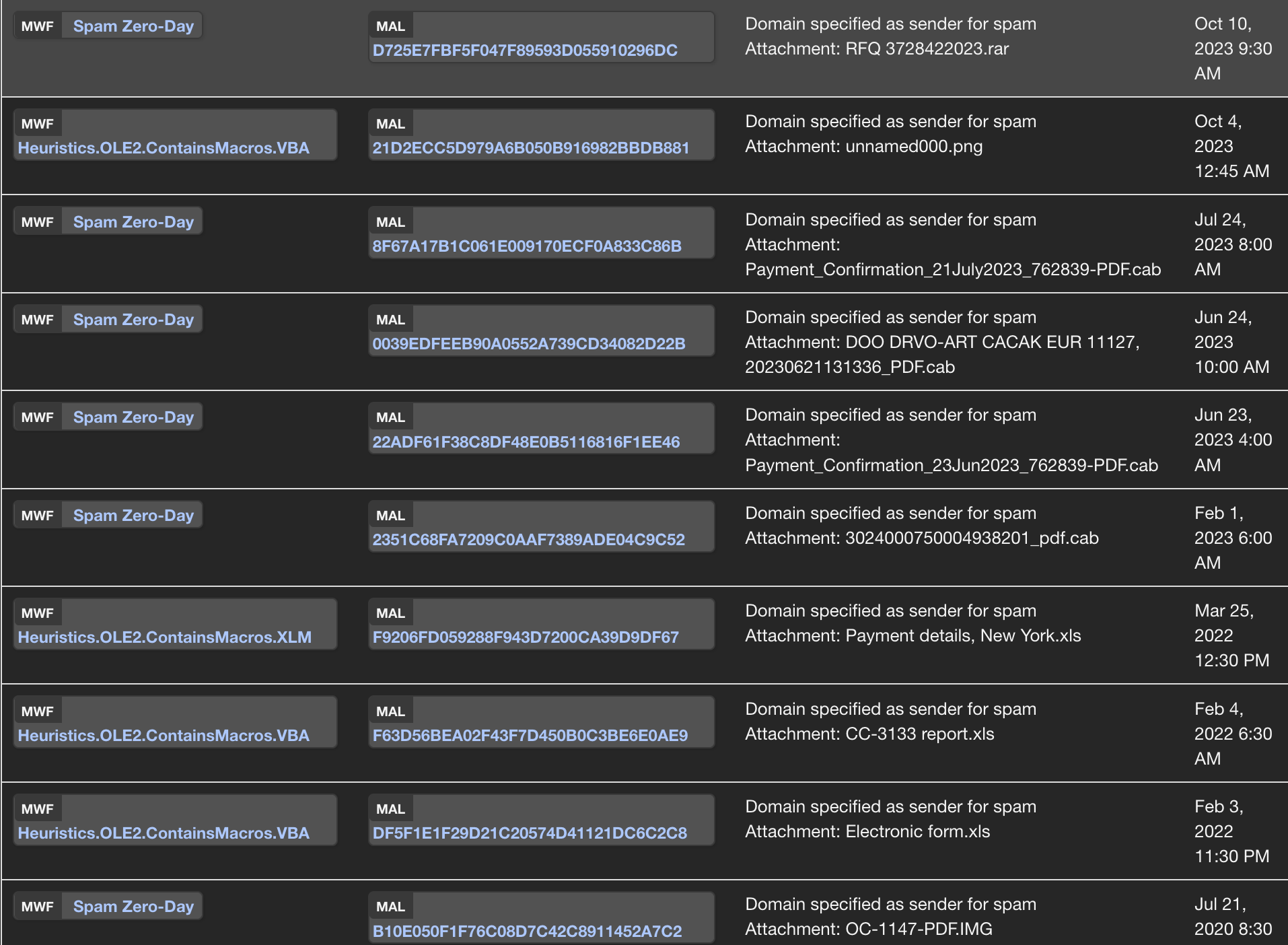
We see that .cab files are commonly used, alongside .rar and .xls
Where’s the breach?
According to a number of online sources, a lot of IDs from mojdoktor.gov.rs have been breached while used for 3rd party services.
However, the sending email in my case (which I redacted for privacy purposes) isn’t listed anywhere but the picture could be bigger.
Zimbra mail software is the one use on mail.mojdoktor.gov.rs, and has a couple of high CVEs since a few years:
 Source: https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-228a
Source: https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-228a
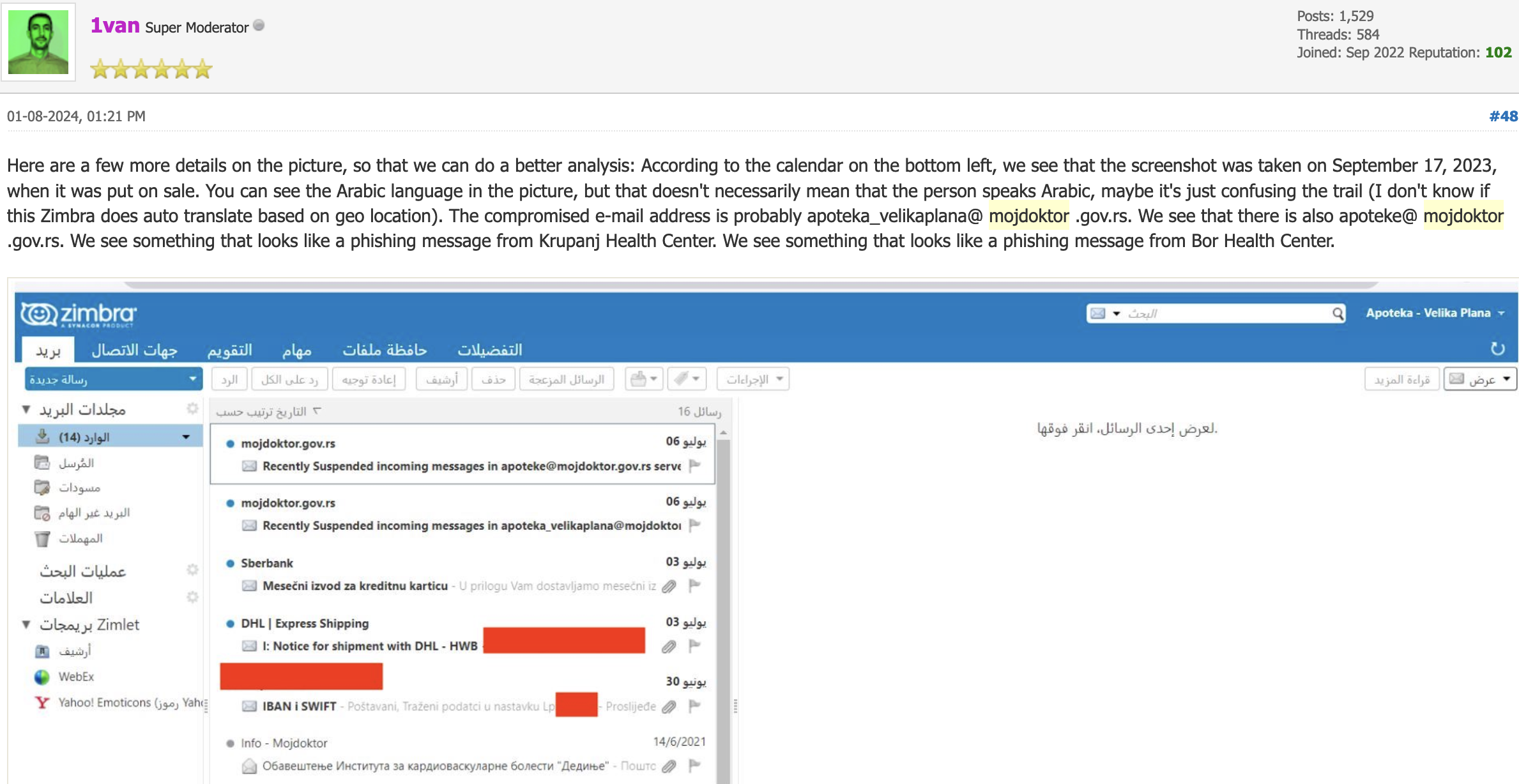
A Serbian forum thread is the only place talking about the potential breach, and a user found some clues about it:
CONCLUSION
Gov domains are widely compromised, and Serbia has been targeted by nation states such as Russia.
An outdated software without any monitoring will most likely be targeted, and here the case is strong.
I contacted the relevant CERT authority, they told me this “issue” is getting resolved.
 Source:
Source: