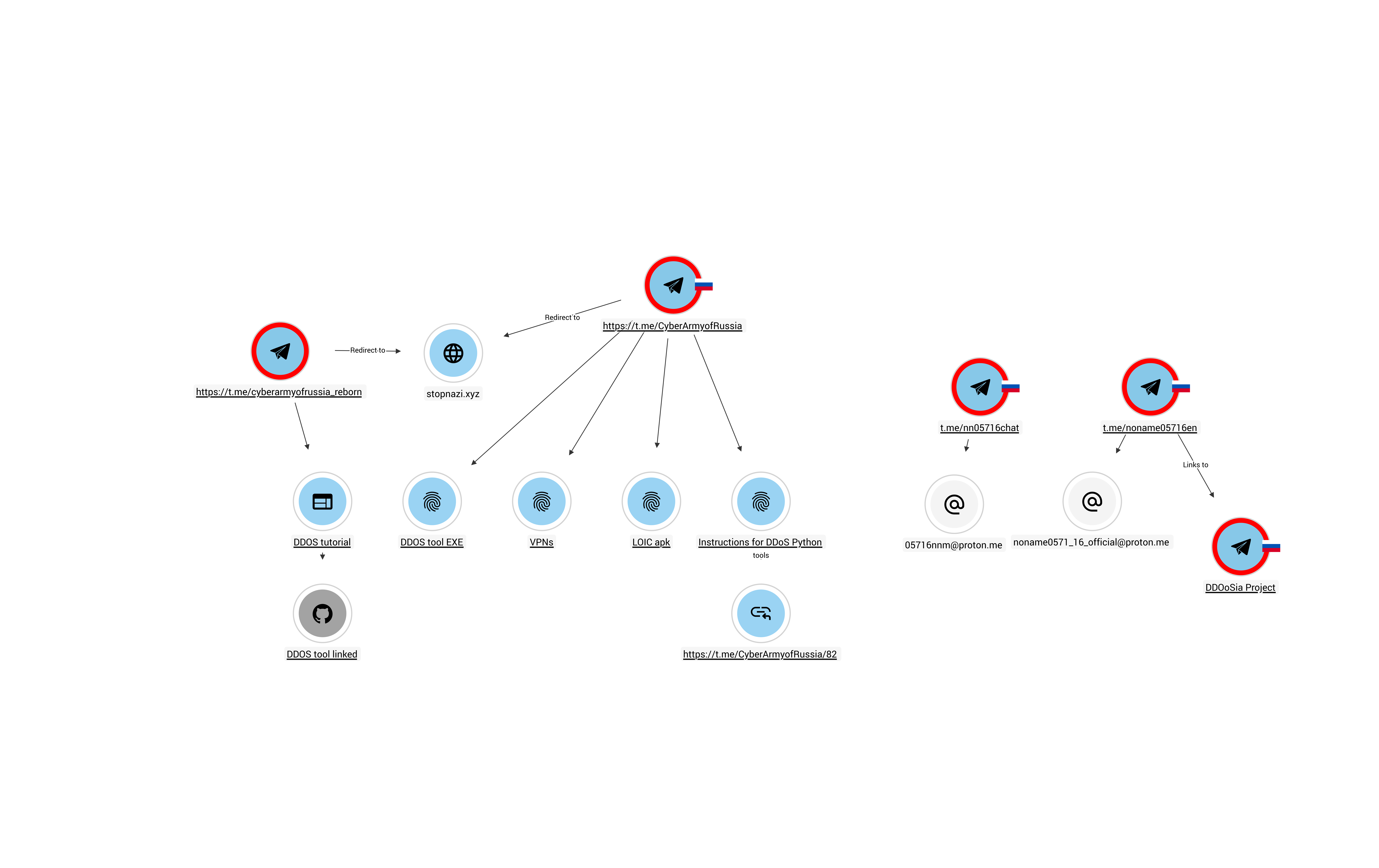
[CTI] NoName057(16) mapping
NoName057(16) is a pro russian hacking group targeting multiple strategic organizations (by DOS/DDOS) associated with countries supporting Ukraine in the ongoing war. They also rely on Botnets (infected machines) to carry large scale attacks. They are very talkative on different platforms, sharing their assets and targets, so I’ll try to summarize all of this here.
NoName057(16) operates on two principal Telegram channels:
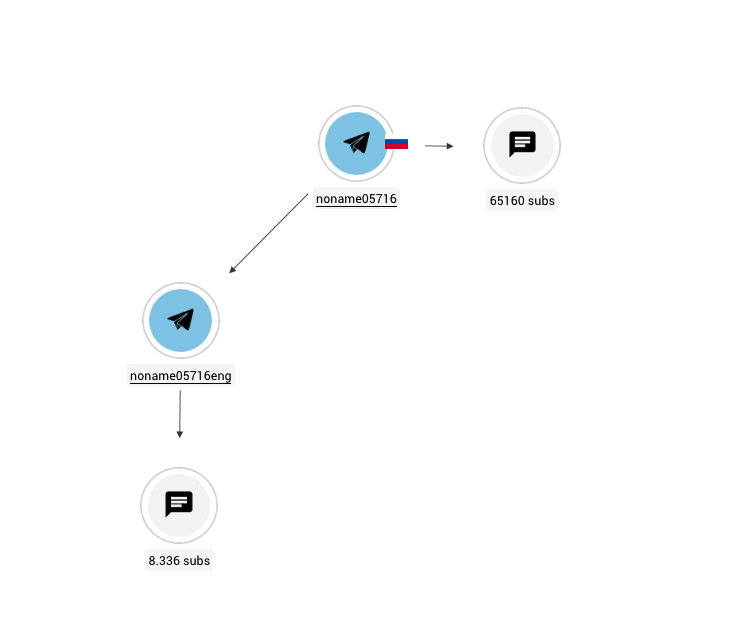
They mainly share news about their attacks:
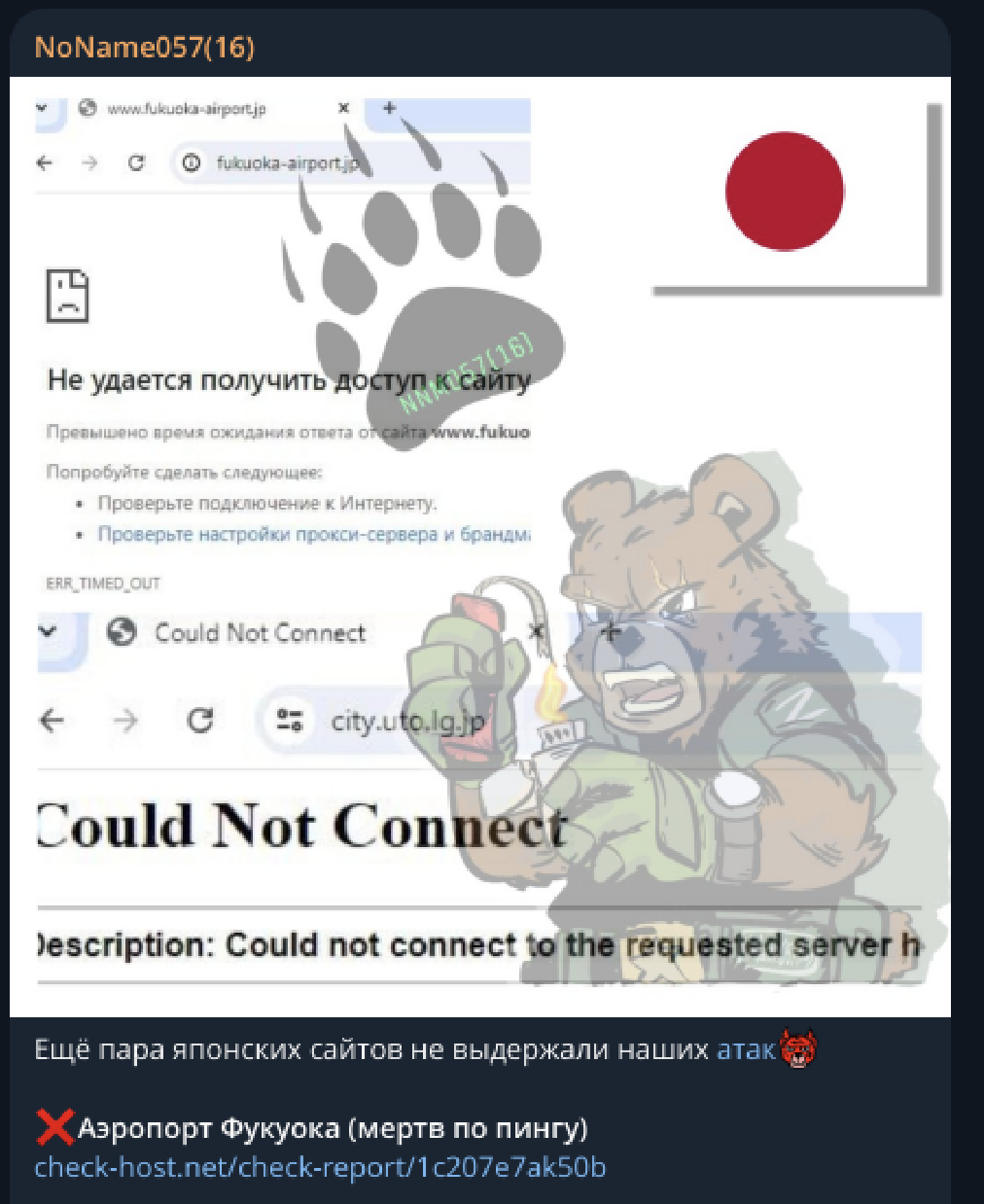
What makes NoName057(16) interesting, is their community implication where anyone can download their DOS/DDOS tools, ask questions and support their actions broadly.
How the attacks happens:
NoName057(16) links other groups to share some tools and methods for amateur cybercriminals:
CyberArmyOfRussia
Here’s a post with direct links:
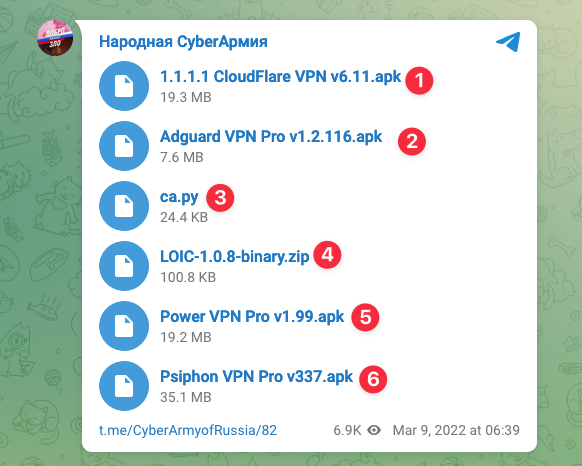
1 - Cloudflare VPN
As seen during attacks, a lot of the offending IPs cames from VPNs to mask the true sender.
2 - Adguard VPN Pro
Same here, just another provider.
3 - ca.py
This is a custom Python script conducts a Dos attack. It uses various techniques to send many requests to the target , with the goal of overwhelming the website’s resources and making it unavailable to users.
4 - LOIC
LOIC (Low Orbit Ion Cannon) is a well known DDOS tool, altough it was popular some years ago, it’s still very effective to break any website. By combining their custom script and LOIC, millions of requests will be generated and impossible to counter at once.
5 - Power VPN
6 - Psiphon VPN
CyberArmyOfRussia has a tutorial to conduct attacks:
Again, we have instructions to launch scripts, and they link a now defunct website that could launch DOS attacks directly on the browser:
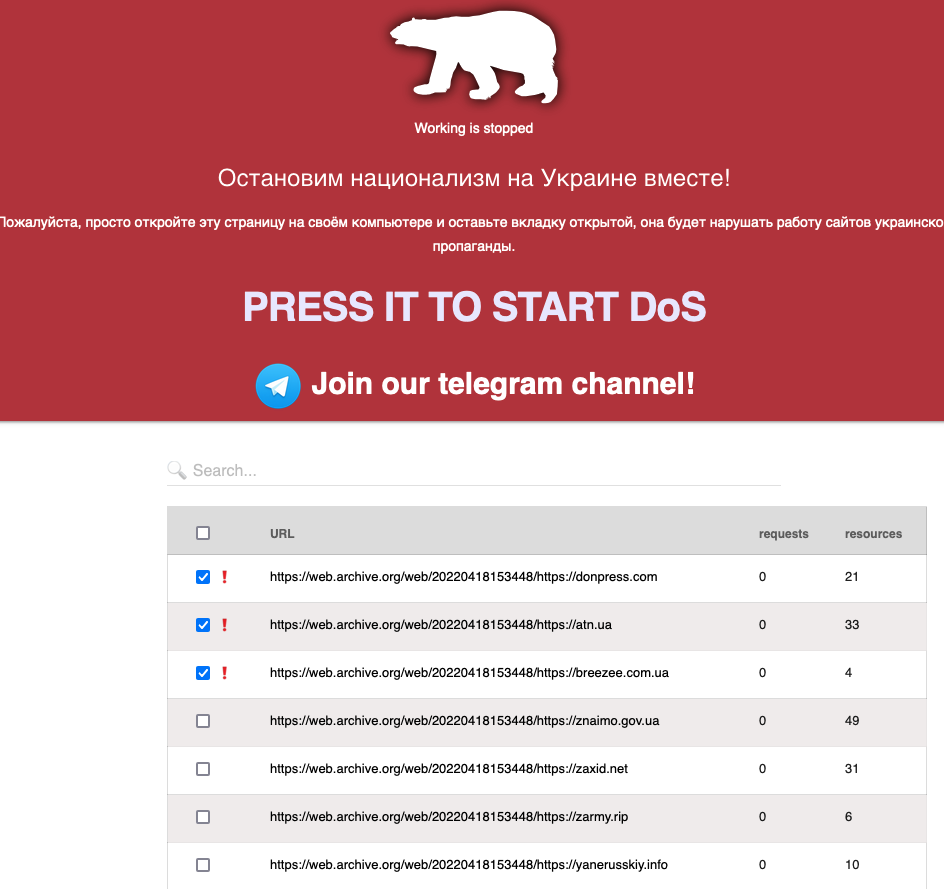
DDoSia Project
DDoSia Project is another group managed by NoName057(16), which also has a Telegram bot to get a list of targets (at the moment, the bot is down).
Instructions provided:
For a more technical analysis, I recommend : https://blog.sekoia.io/Noname05716-Ddosia-project-2024-updates-and-behavioural-shifts/
Why can’t we stop them (from now)?
As these groups shares a list of updated targets, doing continuous CTI helps to counter some attacks, however, by nature, DOS/DDOS are using legitimate processes to query a website or server.
Using a WAF reduces the risks, but not completely at the moment.
The somehow full map of NoName057(16) links: