[OSINT/CTI] Investigating a terrorist IT infrastructure

This article is made for educational purpose only, to show what’s going on behind the scenes of malicious actors and their digital platforms. Everything comes from open and legal sources.
The goal
With the ongoing war between Israeli forces and Hamas, I wanted to analyze different propaganda tools and how they are built.
The target : Al Qassam

The Al-Qassam Brigades is the military wing of the Palestinian organization Hamas. The group is considered a terrorist organization by several countries, including Israel, the United States, the European Union, and others. The Brigades have been involved in numerous attacks against Israeli targets, including suicide bombings, rocket attacks, and other acts of violence.
The front door
It’s no news; terrorist groups have an online presence, sometimes hidden, sometimes very publicly available.
Known domains :
🌐 alqassam.ps
🌐 qassam.ps
🌐 alqassam.net
The TLD “.ps” is for Paltestine; not many registrars support it as it’s not widely used. Keep in mind that WHOIS privacy wasn’t available so long ago, so this information is pretty outdated. Let’s check the domains to see if we can gather useful information:
🌐 alqassam.ps
"createdDate":"2005-04-10T22:00:00+00:00",
"registrantContact": {
"name": "ehab ahmad",
"organization": "",
"street": "gaza",
"city": "gaza",
"state": "",
"postalCode": "",
"country": "PS",
"email": "[email protected]",
🌐 qassam.ps
"createdDate":"2008-04-05T22:00:00+00:00"
"registrantContact": {
"name": "mohammed",
"organization": "",
"street": "der albalh",
"city": "gaza",
"state": "",
"postalCode": "5472",
"country": "PS",
"email": "[email protected]",
🌐 alqassam.net
"createdDate":"2017-07-22T16:24:02+00:00",
"updatedDate":"2022-07-23T07:23:11+00:00",
"expiresDate":"2023-07-22T16:24:02+00:00",
Summary
- alqassam.ps is the oldest domain.
- The registrant’s email is the same; however, it’s not used anymore and is not linked to other services.
- alqassam.net is expired, we’ll see later why.
Social medias :
Main Telegram channel
Al Qassam is primarily sharing their propaganda on Telegram, which contains videos, photos, audios, and links.
Key facts:
Channel created: 09.11.2015
Followers: 570089 (October 2023)
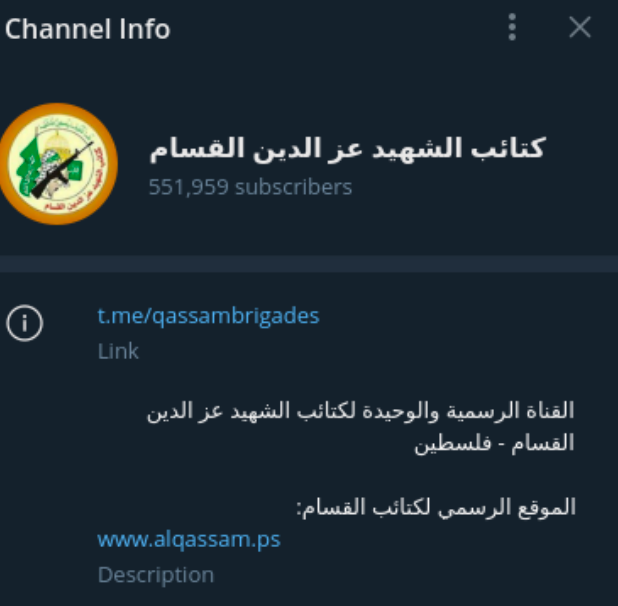
Another channel managed by Al Qassam reposts the same content: https://telegram.me/spokesman_2020
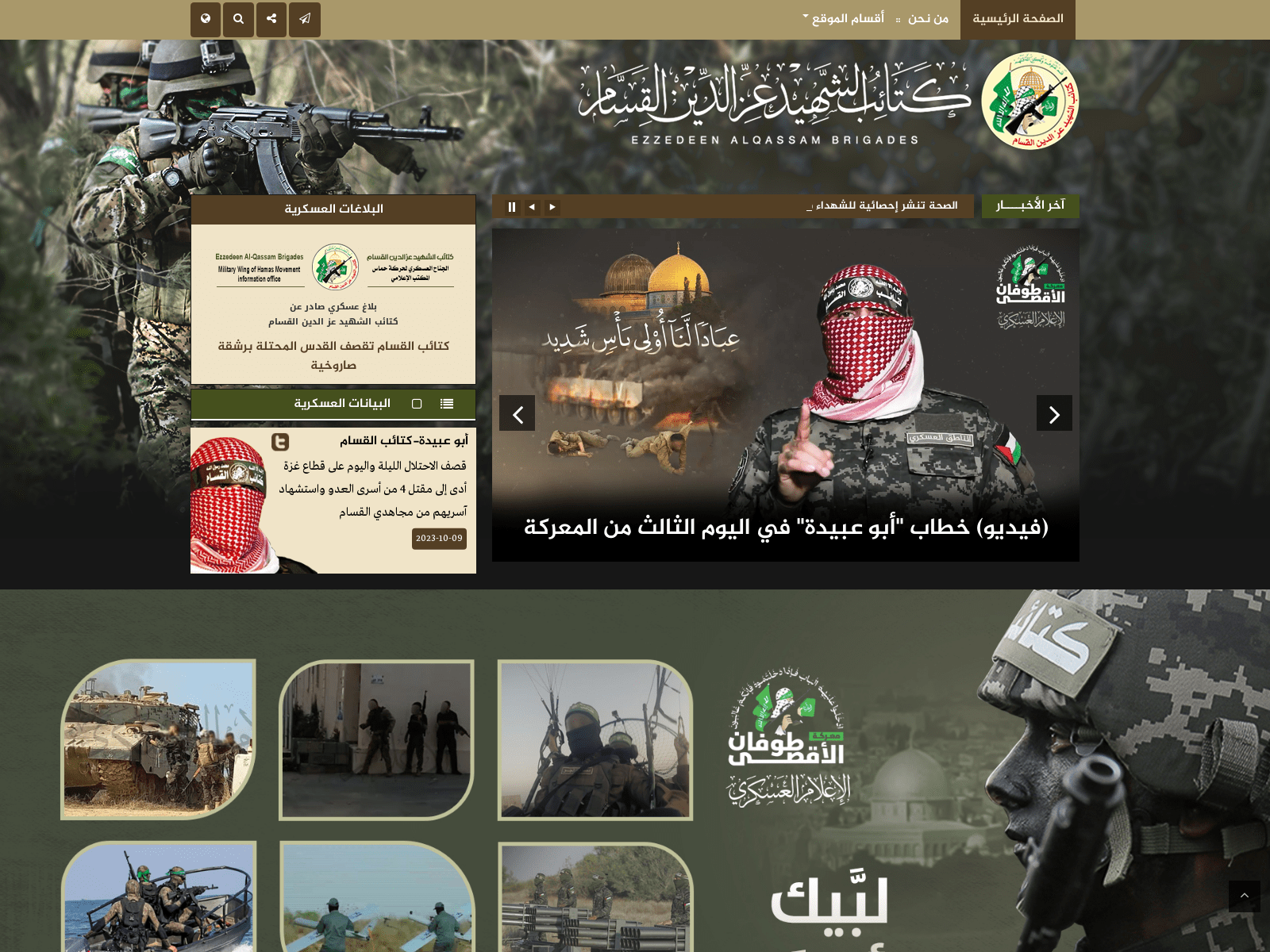
Web analysis
Al Qassam uses a website as their main point of entry.
It contains news, statements, and links to their platforms.
🌐 alqassam.ps
The website is hosted on a Ukrainian server, and the IP seems to only be linked to their domain (+qassam.ps):
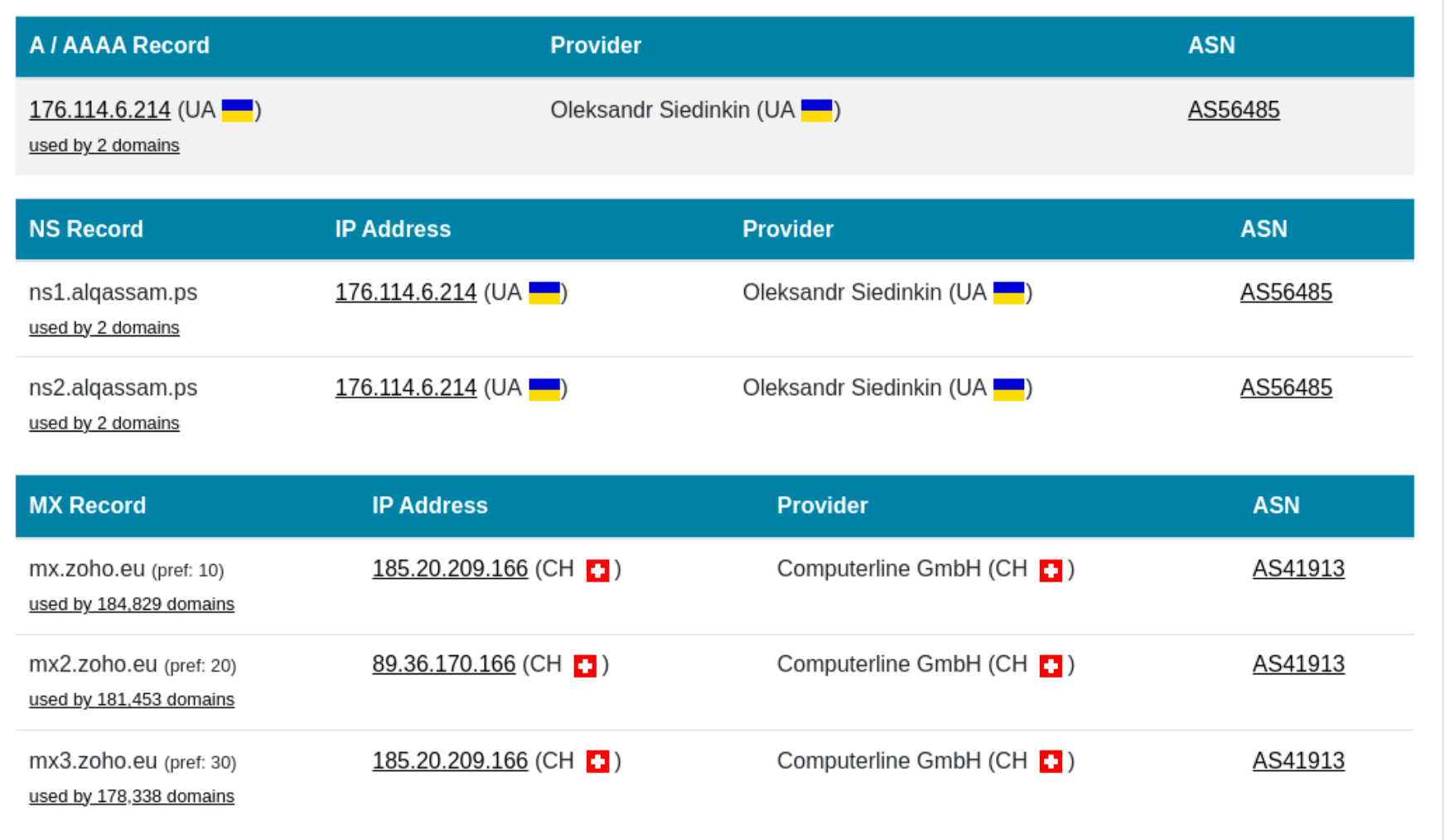
Key facts:
Hosting IP: 176.114.6.214
ASN: AS56485
Website: thehost.ua

Other domains
🌐 mail.alqassam.ps
Interestingly, this domain leads to a query,
https://passport.yandex.ru/auth?from=mail&origin=hostroot_homer_auth_ru&retpath=https%3A%2F%2Fmail.yandex.ru%2F%3Fpdd_domain%3Dalqassam.ps&backpath=https%3A%2F%2Fmail.yandex.ru%3Fnoretpath%3D1&mode=add-user&pdd_domain=alqassam.ps
that redirects to the Yandex ID service:
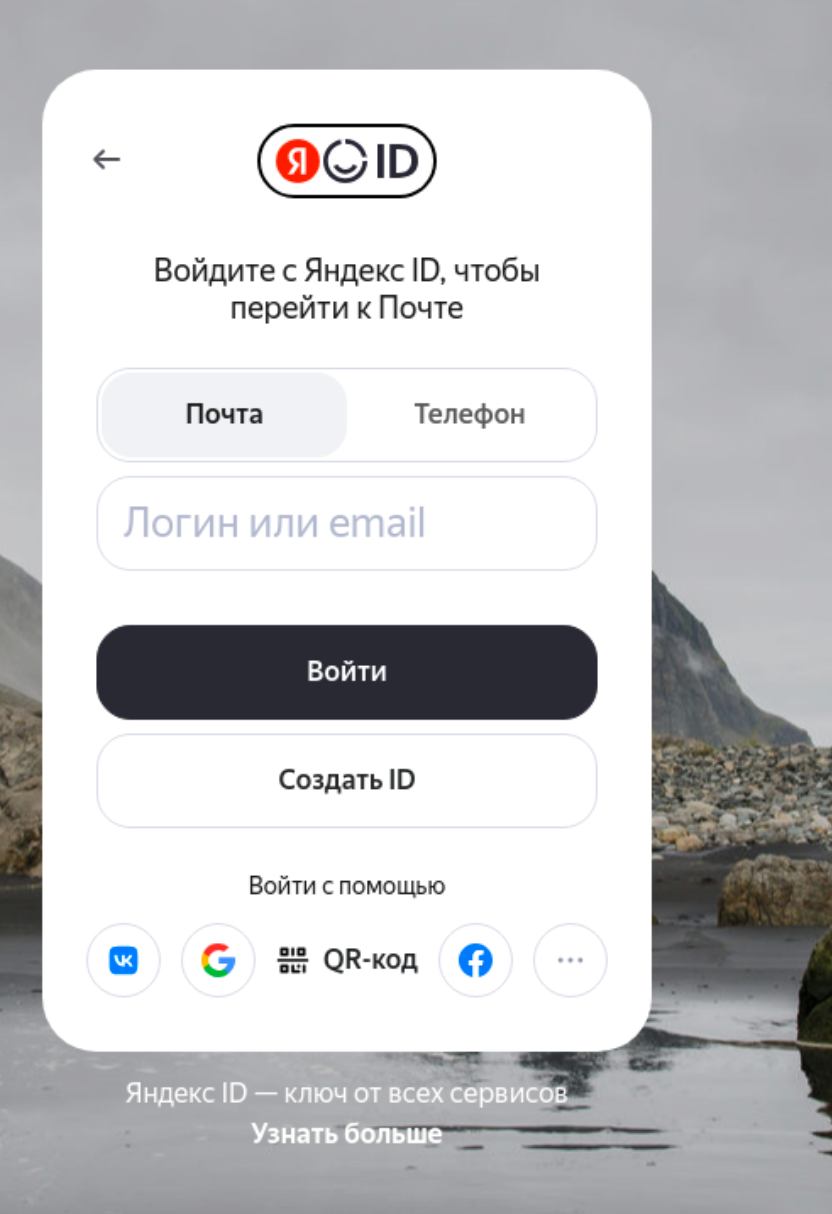
Which makes sense as alqassam.ps uses Yandex MX record:
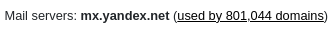
And one of their emails is used on Yandex services:
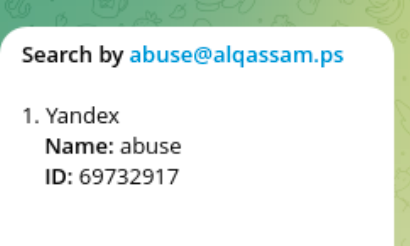
Summary
- From now on, Al Qassam hosts its services between Ukrainian and Russian hosting providers.
🌐 cpanel.en.alqassam.ps
The organization uses Cpanel to manage their hosting platform, pretty usual, but such a solution opens up more possibilities for recon:

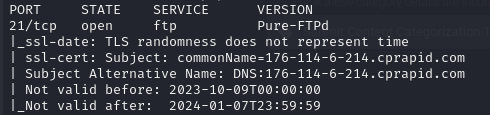
🌐 ftp.alqassam.ps
A FTP server is running, but it does not allow anonymous connections:
🌐 islamic.alqassam.ps
This subdomain is the most interesting in terms of IT; a Fortigate is running behind it. This means a firewall exists and monitors traffic, as well as acting as a watchdog to access other resources. I could not confirm if it was from the hosting company or from Al Qassam, but as the subdomain is directly linked to them, there’s a big probability that more is to be seen with further investigation.
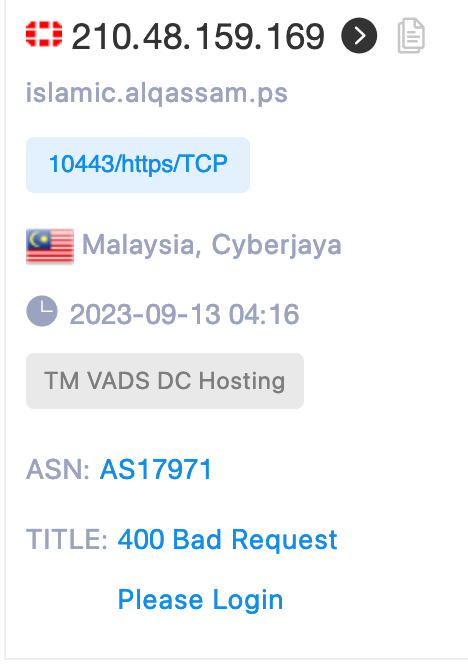
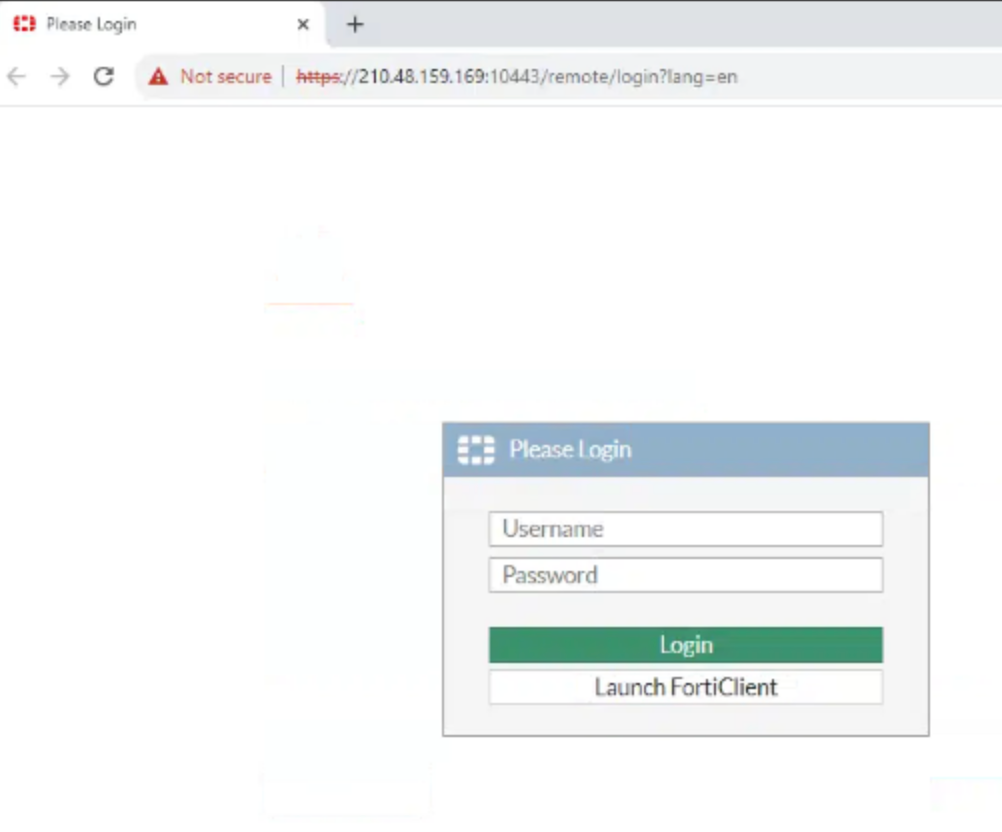
The hosting company is located in Malaysia:
Emails
Mobile app
On their Telegram channel, they released an Android app (mainly a wrapper of the website), which sometimes contains valuable information:
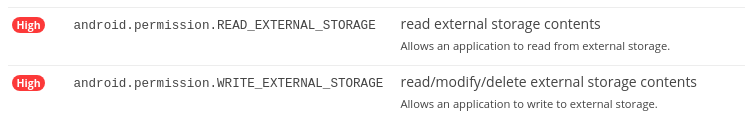
Two critical permissions ares asked:
-
“android.permission.READ_EXTERNAL_STORAGE” allows an application to read from external storage, such as the SD card of a device. It allows the application to access the user’s personal data stored on the external storage. This could include photos, videos, documents, and other sensitive information.
-
“android.permission.WRITE_EXTERNAL_STORAGE” grants the app the ability to modify or write to the user’s external storage (SD card) on an Android device. The potential could be unauthorized Access, Data Integreity etc.
It does not mean the app will abuse the permissions, but coming from a terrorist group, the risks are high.
The app calls for usual domains, except one:
🌐 palcloud.ps
It’s a clone of the the main website:
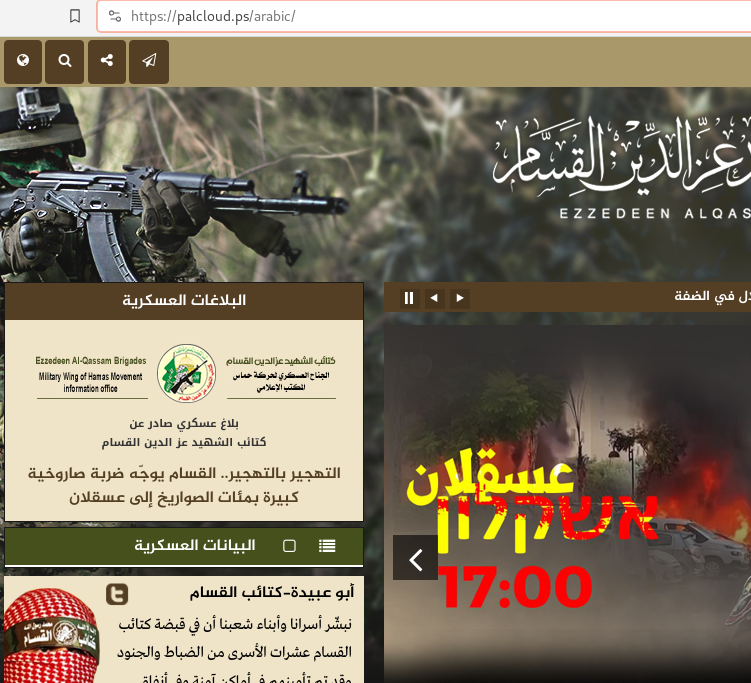
And it’s hosted in Russia:
185.209.31.193
v1888691.hosted-by-vdsina.ru
VDSINA-AS
Russia
Funding
In 2019, Al Qassam shared a funding campaign privilaging Bitcoins as a form of donation.
A couple of posts have been shared with a some phone numbers to be contacted on WhatsApp:
- 📞 First number: +970598091475
The post template on the Telegram channel:
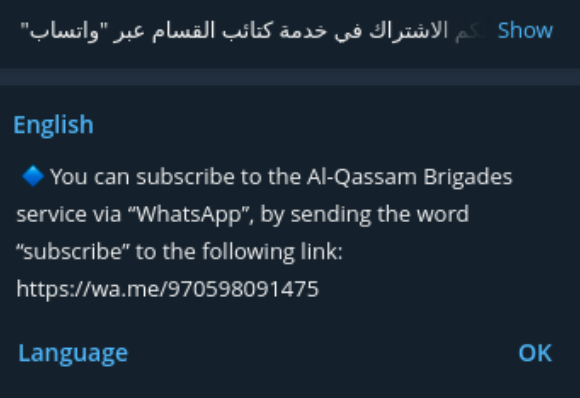
This number is still used on WhatsApp:
Also used on Telegram:
- 📞 Second number: +972599608946
- 📞 Third number: +970598648719
The last numbers are not used on Telegram but still are used on WhatsApp.
This funding effort was distrupted by the Department of Justice alongside FBI, HSI, and IRS agents, seizing wallets and tracking bitcoin exchanges.

Source: https://www.justice.gov/opa/pr/global-disruption-three-terror-finance-cyber-enabled-campaigns
The full complaint can be read here, alongside the Bitcoin addresses and transfers.
CONLUSION
Al Qassam uses a number of platforms for their propaganda, and while it is public, a quick investigation can reveal much more.