[SECURITY] Make MACOS a SECURE and PRIVATE bunker

Image generated on Leonardo.ai
Having used Macos on a daily basis for a few years and experimenting with various techniques and tools, I am now able to suggest a configuration that blends several levels of control with practical usage.
⚠️ A few notes before we start:
- This arrangement is simply mine, and I enjoy it, but it’s not the greatest or definitive.
- Feel free to modify your threat model and look for related subjects.
- I’m just a simple human attempting to share my studies. I personally don’t care if a robust configuration (especially when filtering requests) breaks certain websites, features, or services, but it takes effort to find the ideal compromise.
🔗 Assumptions made here:
- You comprehend various levels of protection, you are well-versed in security and privacy practices, and you realize that not everything can be sufficiently protected if your online activity is vulnerable.
☣️ What we want to counter here:
- Major trackers from the web, whether it’s GAFAM or the myriad domains and IPs invading your queries.
- Surveillance made commonplace by companies, states and other players with unclear intentions.
Threat model definition:
Here’s probably the most important line of this post:
- I don’t trust Apple.
- I don’t need Apple tools such as: find my device, apple music, Icloud etc.
- I utilize proprietary software, but I block the majority of requests.
First configuration:
Congratulations, you just spent a significant amount of money on a piece of hardware (albeit the MacBook Air M1 is still a great deal).
🛑 Don’t connect to Apple
Connecting to your Apple ID during MacBook setup can compromise your privacy. By default, this step enables features like iCloud syncing, which allows Apple to collect data on your browsing history, search queries, and location. Additionally, it may grant access to other personal information, such as contacts, calendars, and email.
🚧 Configuring the firewall
Macos has a simple firewall that does most of the job:
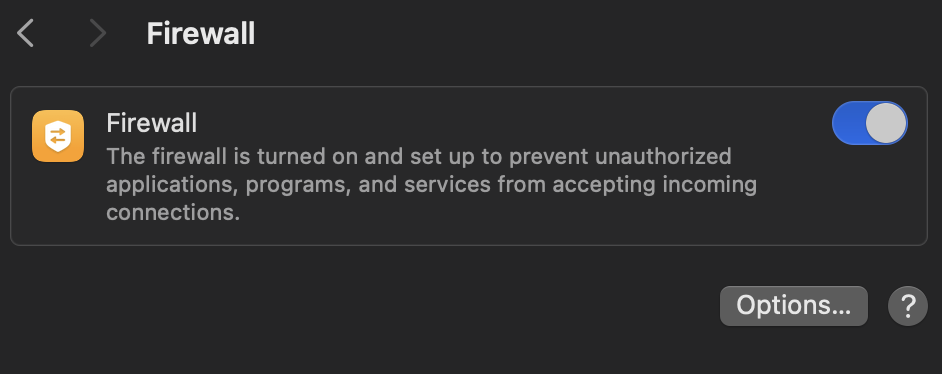
You can setup advanced options, and completly disable all incoming connections made by softwares:
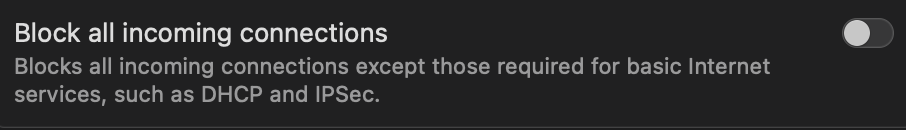
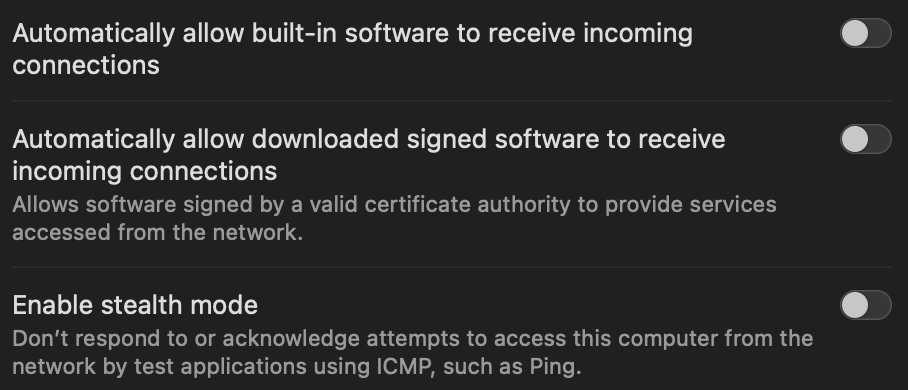
But it does not block all connections, that’s why we’ll have a look later at LittleSnitch and Lulu.
🤺 A better firewall alternative (Murus)
Murus is a great alternative that offers more options to monitor and block services.
You can set the level of blocking according to your need, and customize each service indivdualy (only for the paid version, but that’s really cheap for what it is):
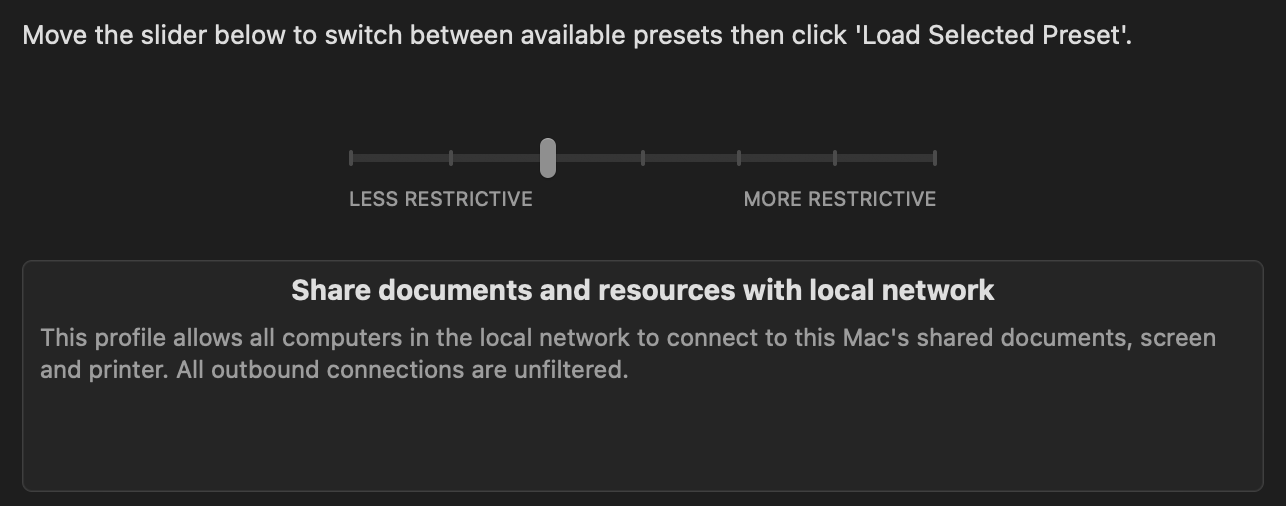
It replicates the Apple lockdown mode at some point, so it’s another tool to consider.
I recommend you take a look at their documentation, and try it out.
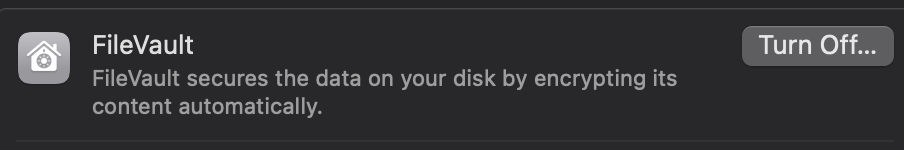
🔒 System encryption
Macos has a built-in feature called FileVault, it encrypts your hard drive, and all data in it. So, theoricaly, if someone wants to dump your disk, they can’t (assuming you have a strong key).
- Per Apple:
If you have a Mac with Apple silicon or an Apple T2 Security Chip, your data is encrypted automatically.
FileVault gives an extra layer, using the XTS-AES-128 encryption algorithm, which is (again) theoricaly strong.
Just turn it on if needed, easy as this:
🔐 Keeping data secure
You have important documents and need to keep them relativly secure ? Here’s a few options:
🧱 Encrypted volume/container
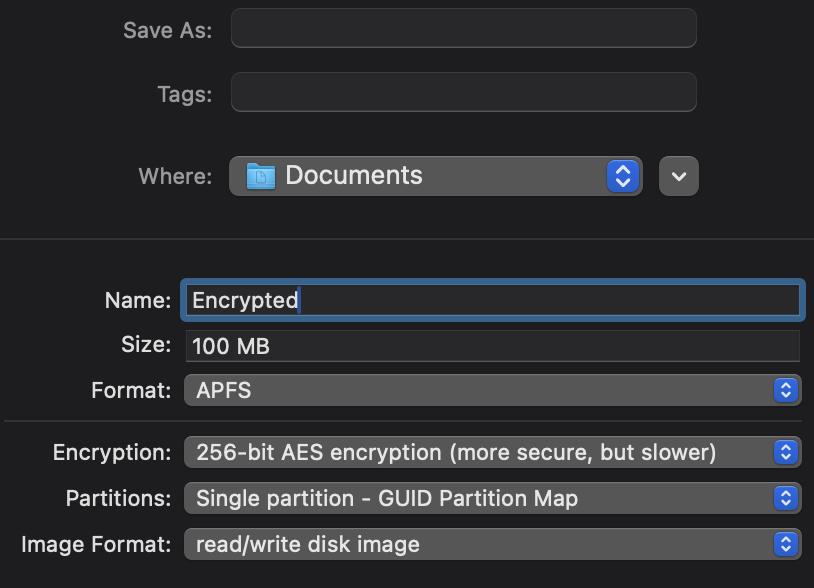
Macos has the ability to create encrypted volumes you can mount using a password, and it’s easy to setup:
- Open Disk Utility
- File –> New image –> Blank image
- Select the location, size and format you need. APFS in 256-bit is recommended:
📝 I recommend to turn off Keychain sync, as someone having direct access to your laptop could just open the vault without putting the password first!
🔑 Veracrypt
Want to have more options and go the open source way?
Veracrypt is your go to. You create a container on any device, setup a STRONG password according to the filesystem you chosed, and voilà!
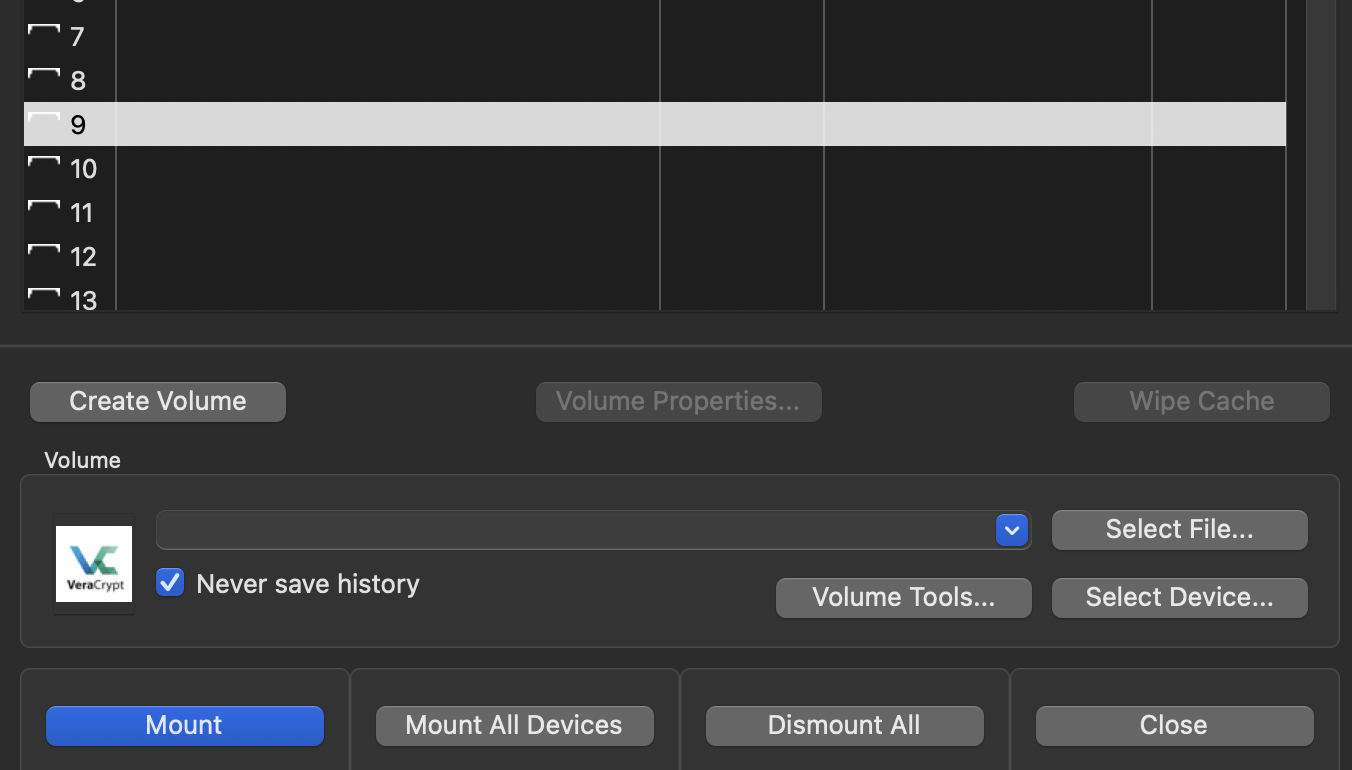
⚠️ For ARM users, you’ll need Macfuse for a seamless compatibility:
📝 A side note about Lockdown mode:
Lockdown mode has been introduced following the Pegasus scandal (https://www.bbc.com/news/technology-57910355).
In short, it’s a simple click to block just about any potentially malicious feature, instead of going through several tools or commands as I present them.
But I recommend having several layers of control no matter what.
🤫 Time to shut off data connections:
Littlesnitch
Little Snitch gives users visibility and control over your computer’s internet connections. You get a detailed breakdown of which apps are accessing the internet, as well as the specific data being transmitted and received.
You can setup blocklists and as the latest version, integrate a private DNS (Nextdns, Adguard…), to have multiple layers of tracking protection.
But it takes a bit of time to setup everything properly, I recommend checking tis tutorial from Inteltechniques:
Lulu
Lulu is pretty much the same, but open source. However you have less configurations capabilities.
Google’s Santa
Sometimes, Google release open tools to protect your devices (not totally evil I guess). You can block binaries nativily to be launched:
Browser
You have a few choices:
- Firefox (modded)
- Librewolf
- Mullvad browser
-
Firefox (modded) By default, Firefox is not really better than chromium based browsers, so you can setup https://github.com/arkenfox/user.js/ inside a profile to have a way better private experience.
-
Librewolf is a fork of Firefox maintained by an independant team. It integrates hardening options by default. Read more here: https://simeononsecurity.com/articles/choosing-librewolf-firefox-privacy-focused-browsers/
-
Mullvad browser
Mullvad released their own Firefox fork, and I personnaly trust their philosophy (read more here: https://mullvad.net/en/blog/mullvad-vpn-was-subject-to-a-search-warrant-customer-data-not-compromised).
In short, they put bigger tracking protection: https://mullvad.net/en/help/tag/mullvad-browser
💡 To compartmentalize your different activities, change browsers according to your habits.
Extensions
-
Ublock origin, the one and only: https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
-
Firefox containers: Allows you to isolate your browsing sessions into separate, temporary containers. Each container has its own set of cookies, storage, and browsing history, which are deleted when the container is closed: https://addons.mozilla.org/en-US/firefox/addon/temporary-containers/
The VPN (endless) debate:
The debate about VPNs often falls into two camps: those who think they’re unnecessary and those who believe they’re essential. My take is that a VPN is just one piece of the puzzle when it comes to protecting our online privacy.
While a good VPN can mask your real IP address, it’s not a foolproof solution. If a website you visit gets hacked and your email and IP address are leaked, you might think you’re safe because the IP address isn’t your real one. However, if that same IP address is found in other data breaches or databases, it can be used to build a detailed profile of you.
This is where the concept of “IP rotation” comes in. Having a single IP address, even if it’s not your real one, can still be a liability. By rotating through multiple IP addresses, you can make it much harder for data brokers and online trackers to build a profile of you.
That’s why I recommend using a VPN that offers multiple IP addresses for each website on their browser extension, such as Mullvad, and combining it with other tools like Firefox containers. This approach can help you stay one step ahead of those who would seek to compromise your online privacy.
Local auditing tools:
-
clamAV (virus auditing tool): https://redgreenrepeat.com/2019/08/09/setting-up-clamav-on-macos/
Conclusion
That was my 2 cents about it, feel free to contact me for adjustments or questions.